Privileged Access Management (PAM) is an essential element of an organization’s security infrastructure, helping to manage, control, and monitor privileged user activities. The increasing sophistication of cyber threats, the widespread adoption of cloud services, and the demand for remote work have made PAM more important than ever. PAM is a robust defense layer, ensuring that privileged accounts with extensive access rights across an organization’s network remain safeguarded from unauthorized access and potential misuse. It’s the critical barrier between cybercriminals and your most sensitive data and systems.
As we delve into the intricacies of developing and enhancing a PAM Architecture Strategy, it is crucial to grasp PAM’s role in today’s digital environment. The PAM strategy is not a mere implementation of tools but an overarching approach that aligns with an organization’s cybersecurity framework. It operates on the principle of providing the least privileges necessary for a task to minimize potential attack surfaces. By taking the time to understand, implement, and enhance your PAM strategy, you position your organization to anticipate better, prevent, and respond to the ever-evolving landscape of cyber threats.
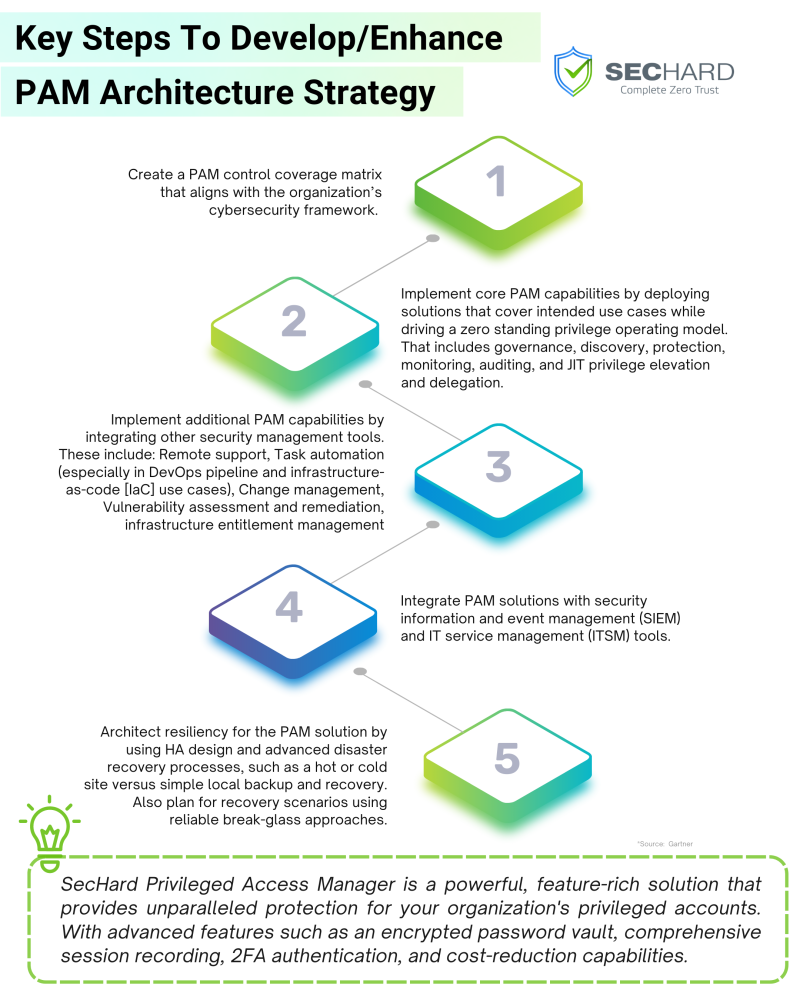
Key Steps To Develop/Enhance PAM Architecture Strategy
- Formulating a PAM Control Coverage Matrix
- Implementing Core PAM Capabilities
- Integrating Additional PAM Capabilities
- Integrating PAM Solutions with SIEM and ITSM Tools
- Architecting Resiliency for PAM Solution
1. Formulating a PAM Control Coverage Matrix
The first step towards building a resilient PAM architecture strategy is formulating a PAM Control Coverage Matrix. This robust foundation paves the way for an all-encompassing cybersecurity framework within your organization. The matrix is a meticulous inventory mapping all the privileged access controls deployed across your systems. It identifies where these controls are positioned, their functionality, and the assets they protect.
Developing a PAM Control Coverage Matrix requires an in-depth understanding of your organization’s internal landscape and the external threats it faces. It enables you to visualize the distribution of access controls, reveals gaps in your security posture, and pinpoint areas requiring attention or enhancement. The matrix needs to be dynamic, facilitating frequent updates and modifications, considering the evolving nature of cyber threats. A well-structured matrix serves as a compass, guiding your organization toward achieving its cybersecurity goals and maintaining a solid PAM stance.

2. Implementing Core PAM Capabilities
After creating the PAM Control Coverage Matrix, the next step is implementing core PAM capabilities. These capabilities provide a bulwark against internal and external threats and form the basis of the zero-standing privilege model. Core PAM capabilities encompass governance, discovery, protection, monitoring, auditing, and just-in-time (JIT) privilege elevation and delegation.
Governance entails defining clear policies and roles, while discovery involves locating and cataloging all privileged accounts across your infrastructure. The protection ensures that these accounts are secured from unauthorized access, and monitoring involves constant vigilance of all privileged activities to detect unusual behavior. Auditing entails maintaining a record of all privileged access and helping in investigations and compliance. JIT privilege elevation and delegation grant privileges to users only when needed, minimizing the attack surface.

3. Integrating Additional PAM Capabilities
PAM capabilities can be enhanced by integrating additional security management tools, which provide more layered defense and optimized operational processes. These include remote support for seamless access, task automation to minimize manual errors, change management to effectively control system modifications, and vulnerability assessment and remediation to identify and patch vulnerabilities.
Infrastructure entitlement management, another additional PAM capability, provides an overview of who has access to what resources, ensuring better control over privileged accesses. This additional layer of PAM capabilities enhances the organization’s security stature, helps manage risks more efficiently, and improves overall operational efficiency.

4. Integrating PAM Solutions with SIEM and ITSM Tools
An effective PAM strategy also integrates PAM solutions with security information, event management (SIEM), and IT service management (ITSM) tools. SIEM tools provide real-time security alert analysis, helping detect potential security incidents. They gather log and event data from various sources, identifying patterns and signaling alerts for unusual activities.
ITSM tools, on the other hand, handle all the processes related to the delivery of IT services within an organization. When PAM solutions are integrated with SIEM and ITSM, a seamless flow of information improves the incident response time and reduces the risk of security breaches. This integration also aids in maintaining the overall system health and boosts productivity.
5. Architecting Resiliency for PAM Solution
The final step in developing an effective PAM architecture strategy is architecting resiliency for the PAM solution. This involves creating a high-availability (HA) design and implementing advanced disaster recovery processes. An HA design ensures that your PAM solution remains available even if some components fail, while advanced disaster recovery processes protect against data loss during a disaster.
Additionally, planning for recovery scenarios using reliable break-glass approaches ensures you have emergency access to critical systems in crisis situations. Architecting resiliency into your PAM solution protects your organization from expected and unexpected threats, ensuring that your critical systems can rapidly recover and return to normal operations.
SecHard Zero Trust Orchestrator: Transform Your Cybersecurity Strategy with SecHard PAM
Choosing the right Privileged Access Management system is pivotal for every organization’s cybersecurity framework. With SecHard’s PAM, you’re choosing more than just privileged access; you’re choosing comprehensive, adaptable, and reliable cybersecurity. Our solution provides privileged access to the right individuals. It implements the essential Protection Visibility Control (PVC) across all network devices and computers used in the connection, adhering to Zero Trust Architecture (ZTA) principles.
SecHard PAM stands out because we can automatically discover new assets, perform automatic security hardening scoring, and enforce predefined hardening settings fully. Already have a PAM product? Don’t fret. SecHard is designed for compatibility and can seamlessly integrate with third-party PAM products to assess their security hardening scores.
Don’t leave your cybersecurity to chance. Contact us at [email protected] to explore how SecHard Privileged Access Manager can fortify your defenses. Ready to see it in action? Book a free demo today at https://lnkd.in/dt6PPvTr and see firsthand why SecHard is the ideal cybersecurity partner for your organization.
