Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
Configuration security is an important element in the ZTA. SecHard performs security hardening checks with great success and speed. Beyond the security hardening, configuration and device management tasks are also performed by SecHard.
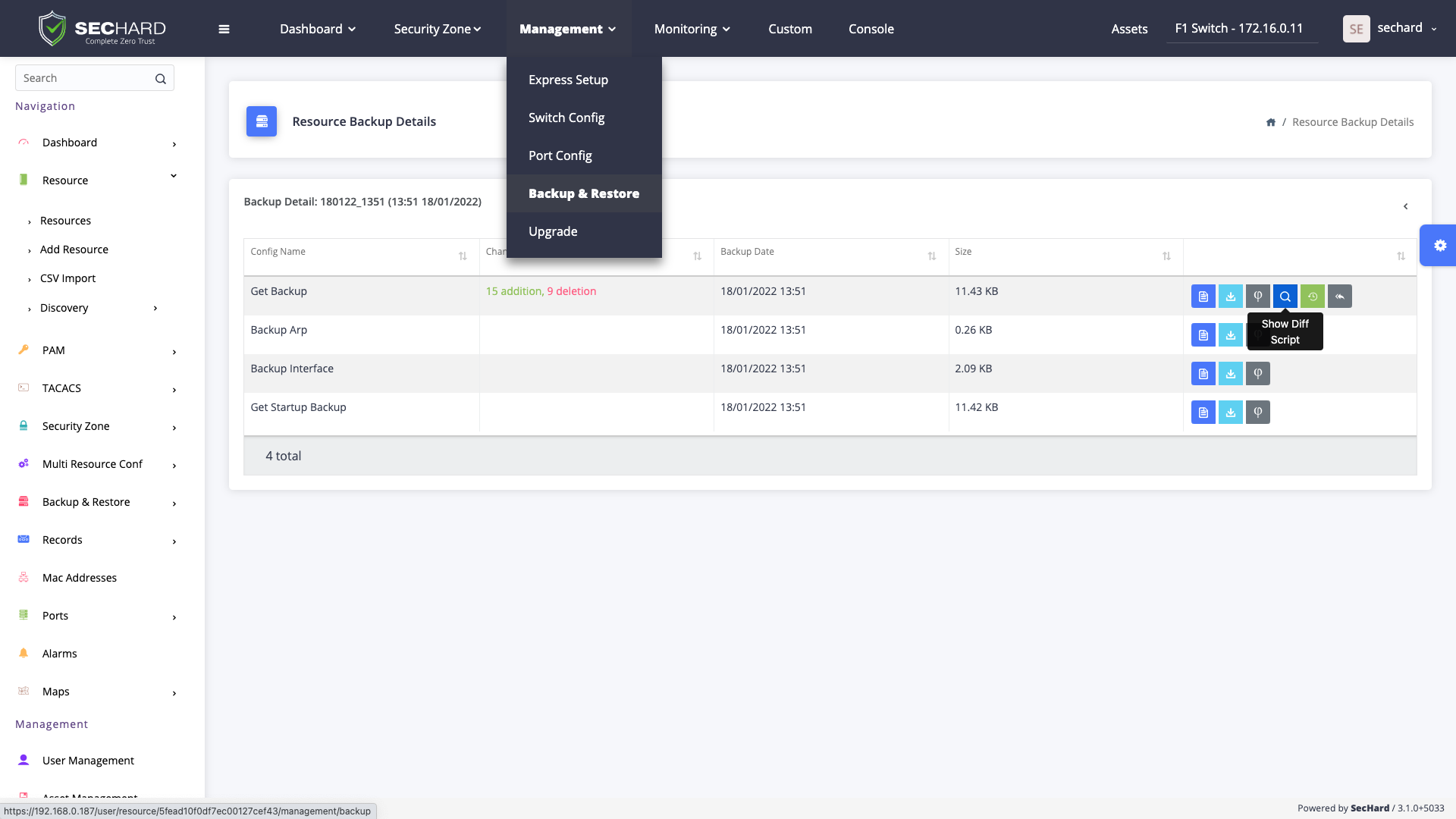
Configuration backup and restore operations of network devices can be done centrally by SecHard. In addition to security configurations, SecHard can automatically manage and monitor all configuration changes on the assets it manages. SecHard also sends configuration changes on multiple devices.
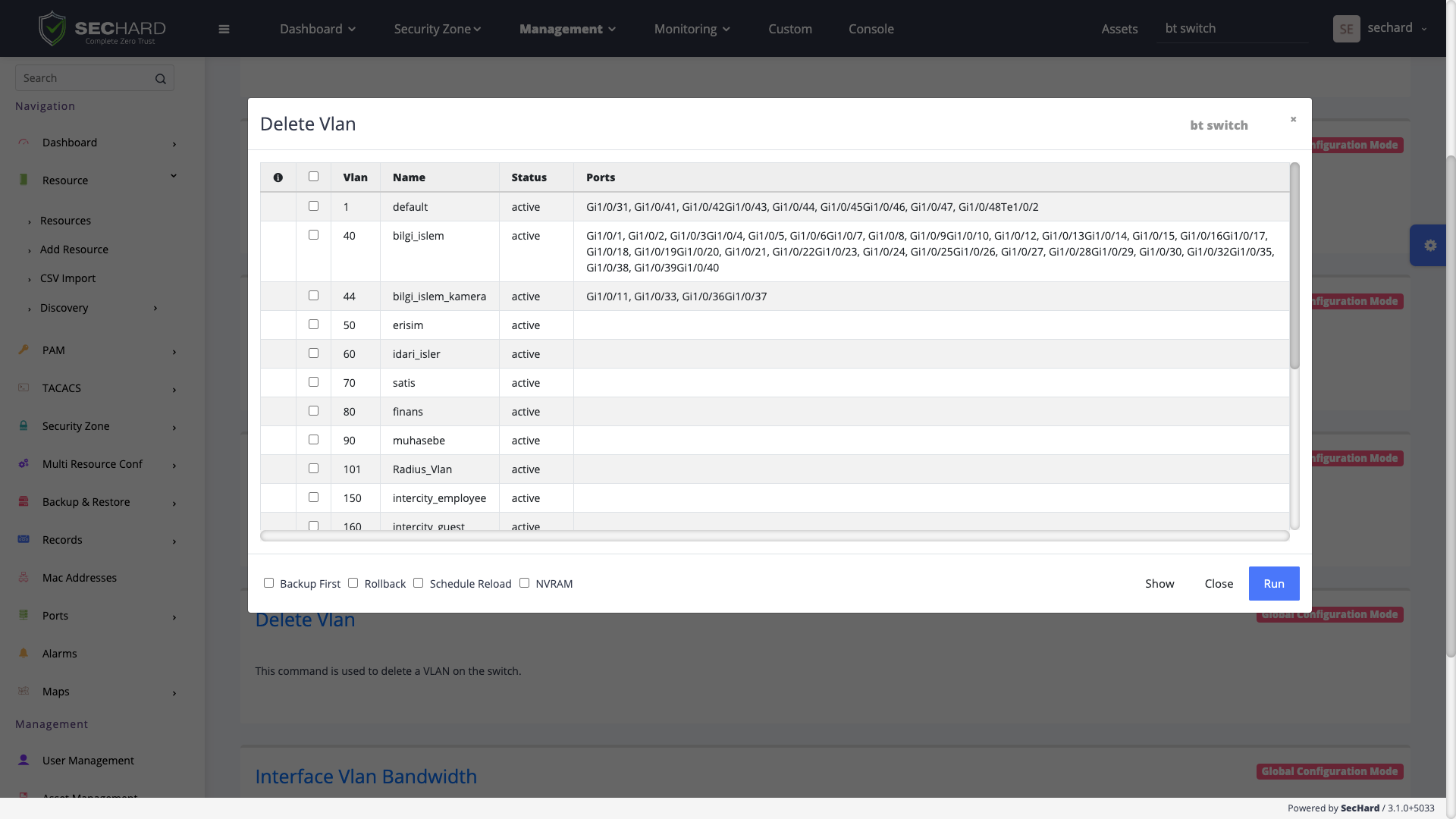
For network devices, the number of ports and their status, the details of the traffic passing through the ports, CPU, and RAM usage are monitored by SecHard. Alarms can be triggered when critical events occur. Operational tasks such as creating a VLAN on network devices can be easily performed through the SecHard user interface with a few clicks without the need to know the CLI commands.
In order for network devices to be able to remediate vulnerabilities previously detected by SecHard, their firmware can be upgraded through the SecHard user interface.
Making port security settings is vital to prevent attacks such as ARP Spoofing, STP Manipulation, and DHCP Starvation that can be made due to insecure configuration of network devices. SecHard checks whether the port security settings have been made correctly or not. Network devices with missing port security configurations can be automatically remediated with SecHard. It can also disable ports that are not used for a certain period of time and assign them to a passive VLAN.
Thanks to these features, it provides security for network devices even in areas untouched by global security hardening authorities and regulations.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
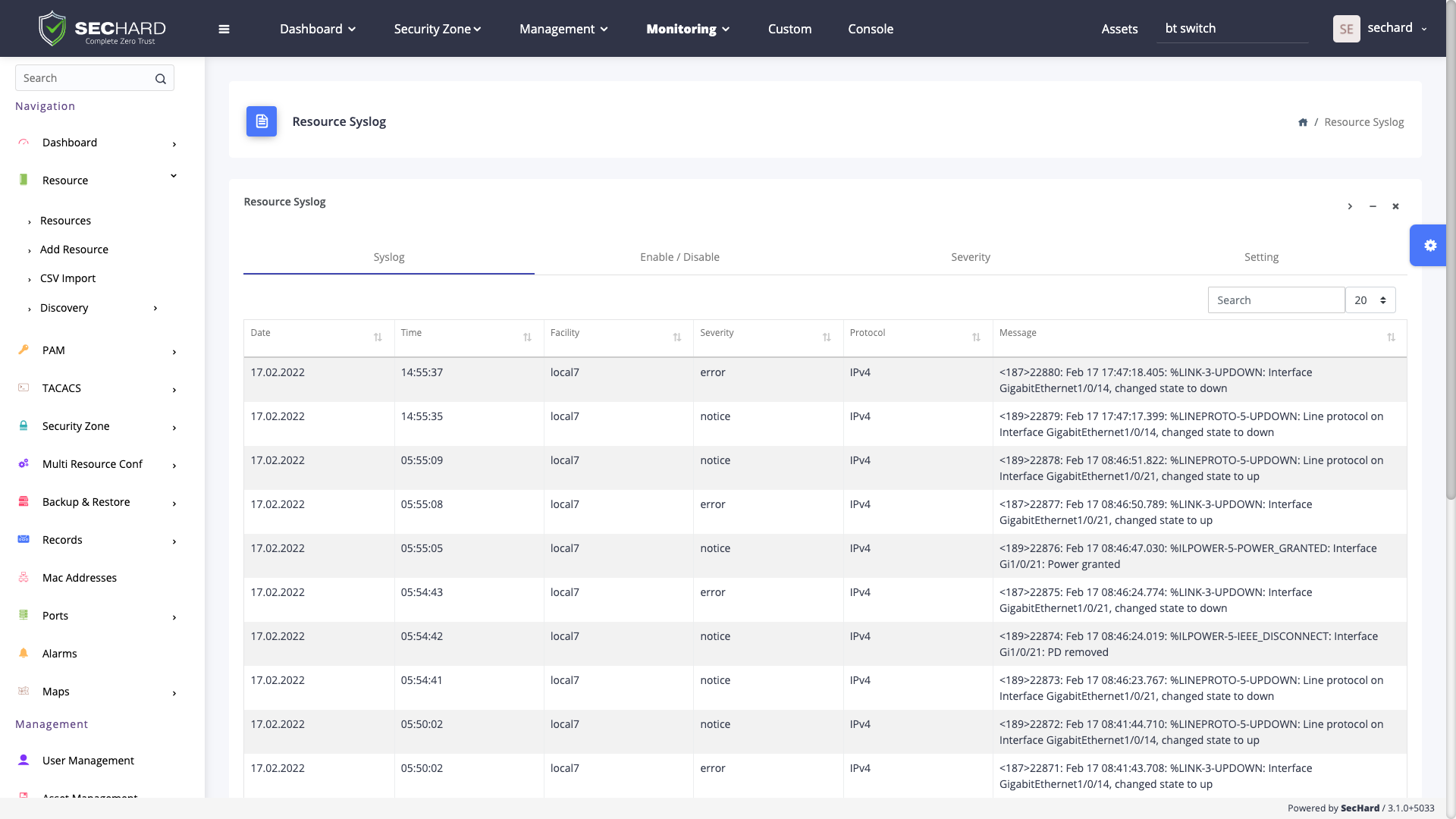
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
