Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
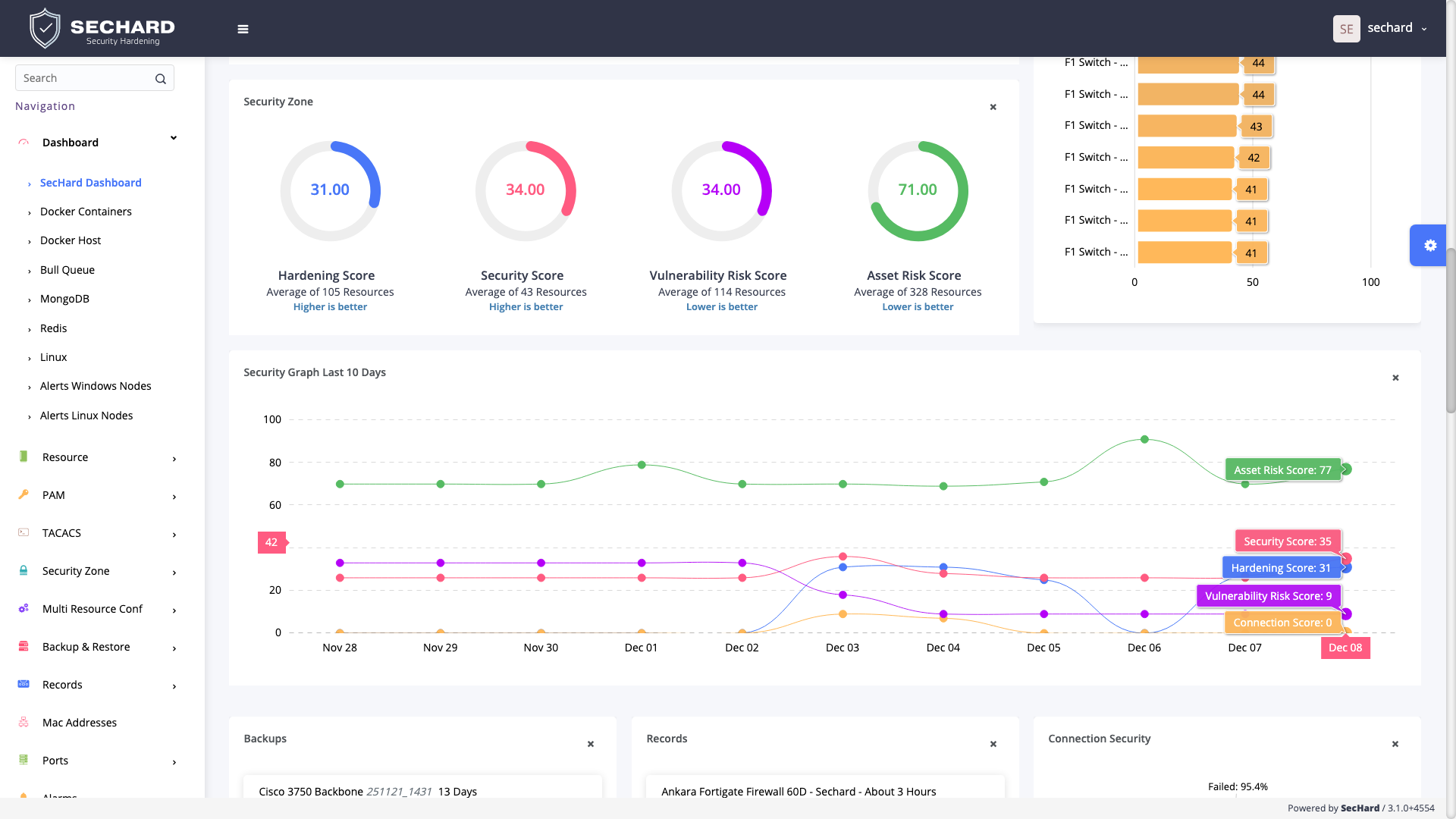
The biggest problem that the industry has not been able to respond to is the inability to holistically score and manage business risks along with technical risks. In every ISO27001 Information Security Management System (ISMS) compliance analysis, business risks are scored but doomed to live in an Excel cell. In fact, these scores are not actually used anywhere.
SecHard combines business and technical risks and calculates real-world risk scores. It measures and scores the technical security risks of assets or asset groups with its own security hardening, vulnerability management, and asset management modules.
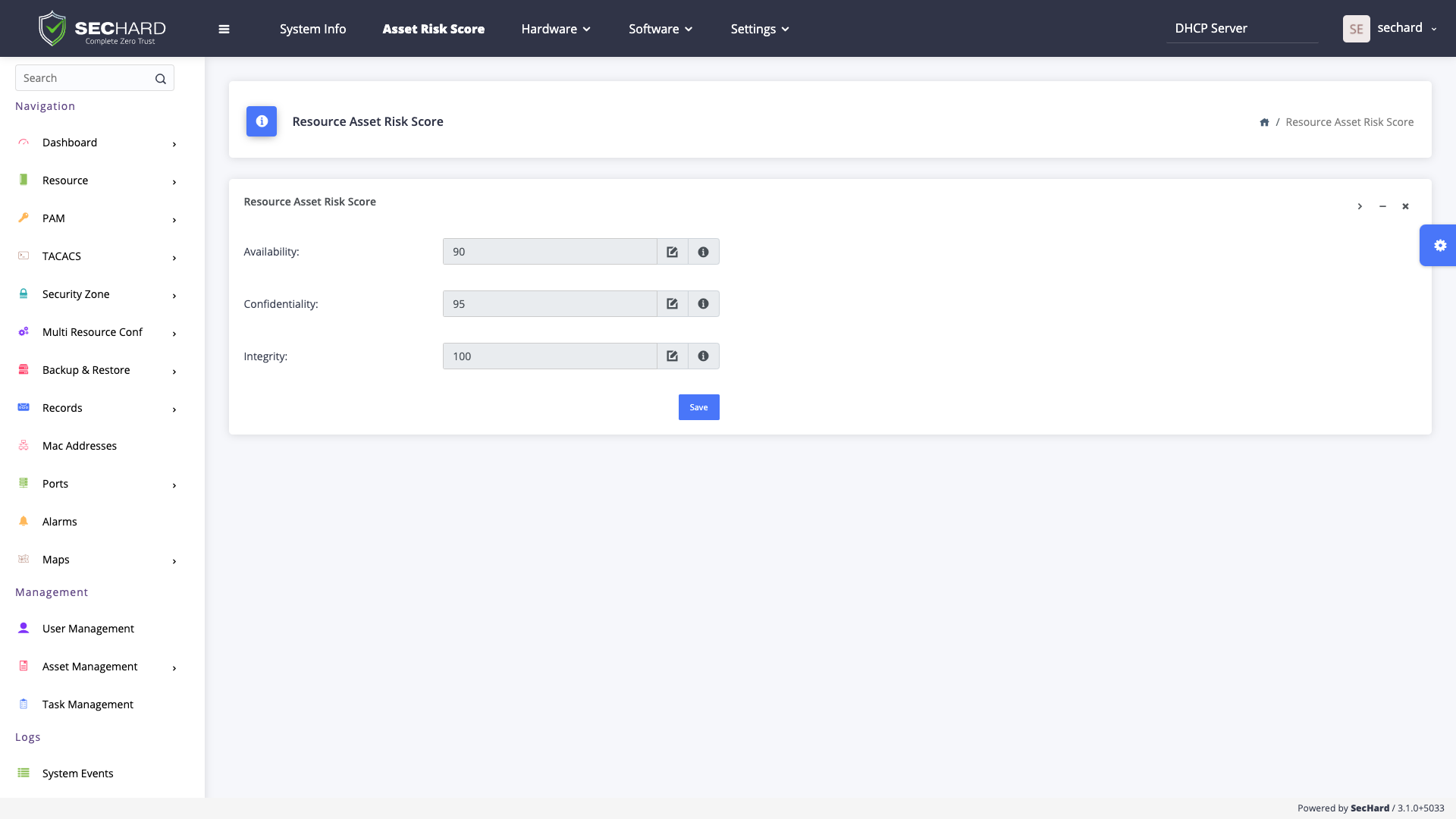
Security risk scored by information security teams for ISO 27001 ISMS and similar regulations can be added to SecHard’s Asset Management Module. Besides, technical scores and business scores can be integrated by SecHard risk algorithm, which determines the real-world risk score.
SecHard has the security hardening remediation feature to reduce technical risk scores after determining the real-world risk score. At the same time, thanks to the Trellix (McAfee Enterprise) integration, SecHard makes it possible for conventional security software to provide instant security by automatically triggering hardened Endpoint Security, DLP, EDR, and TIE configurations for assets above the acceptable risk level.
In large enterprises Governance, Risk and Compliance (GRC) products are used to manage risks. SecHard can associate SecHard assets with asset groups in GRC and automatically takes asset or asset group risk scores from the GRC. Thanks to this integration, asset and asset groups scores can be automatically imported from the GRC and necessary security controls can be automatically operated by SecHard according to the risk level.
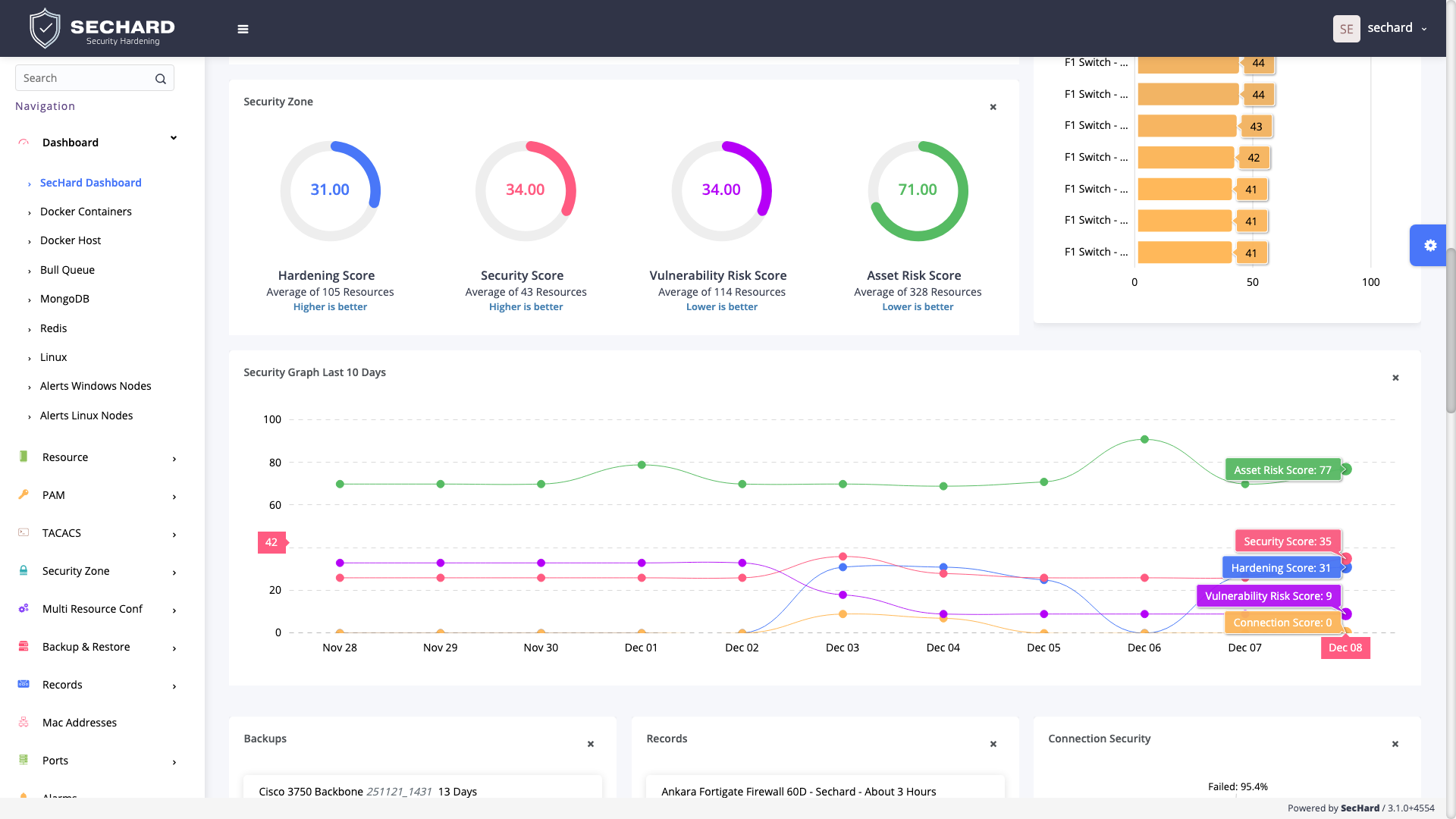
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Zero Trust and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
