Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
The most important PVC in Cyber Hygiene Platform is People. Studies have found that 77% of data leaks are caused by privilege abuse3, which proves the importance of this control. Due to the difficulty of identity management, many different types of threats can arise ranging from espionage to ransomware.
Unlike a traditional PAM product, SecHard offers a PAM solution that integrates with other PVC areas recommended by the Cyber Hygiene Platform. SecHard not only gives privilege access to the right person, but also performs the recommended PVCs that are required for the ZTA on all the network devices used in the connection, and on the computer that makes the connection. In this way, the computers whose hardening or security scores produced by SecHard are below the acceptable security level can be restricted from authorized access or risk warnings can be generated. SecHard can automatically discover and login new assets, perform automatic security hardening scoring, and remediate predefined hardening settings fully automatic.
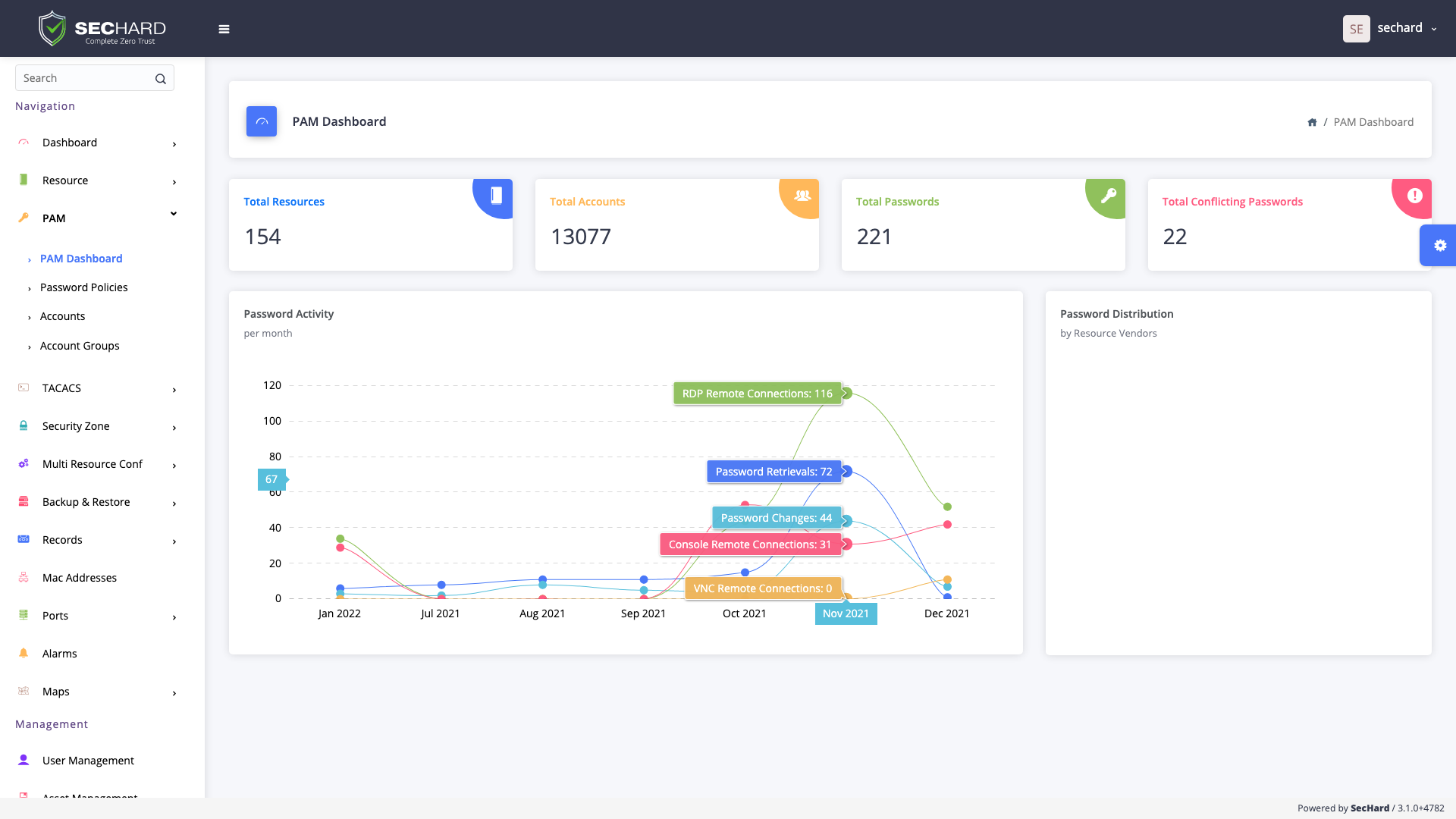
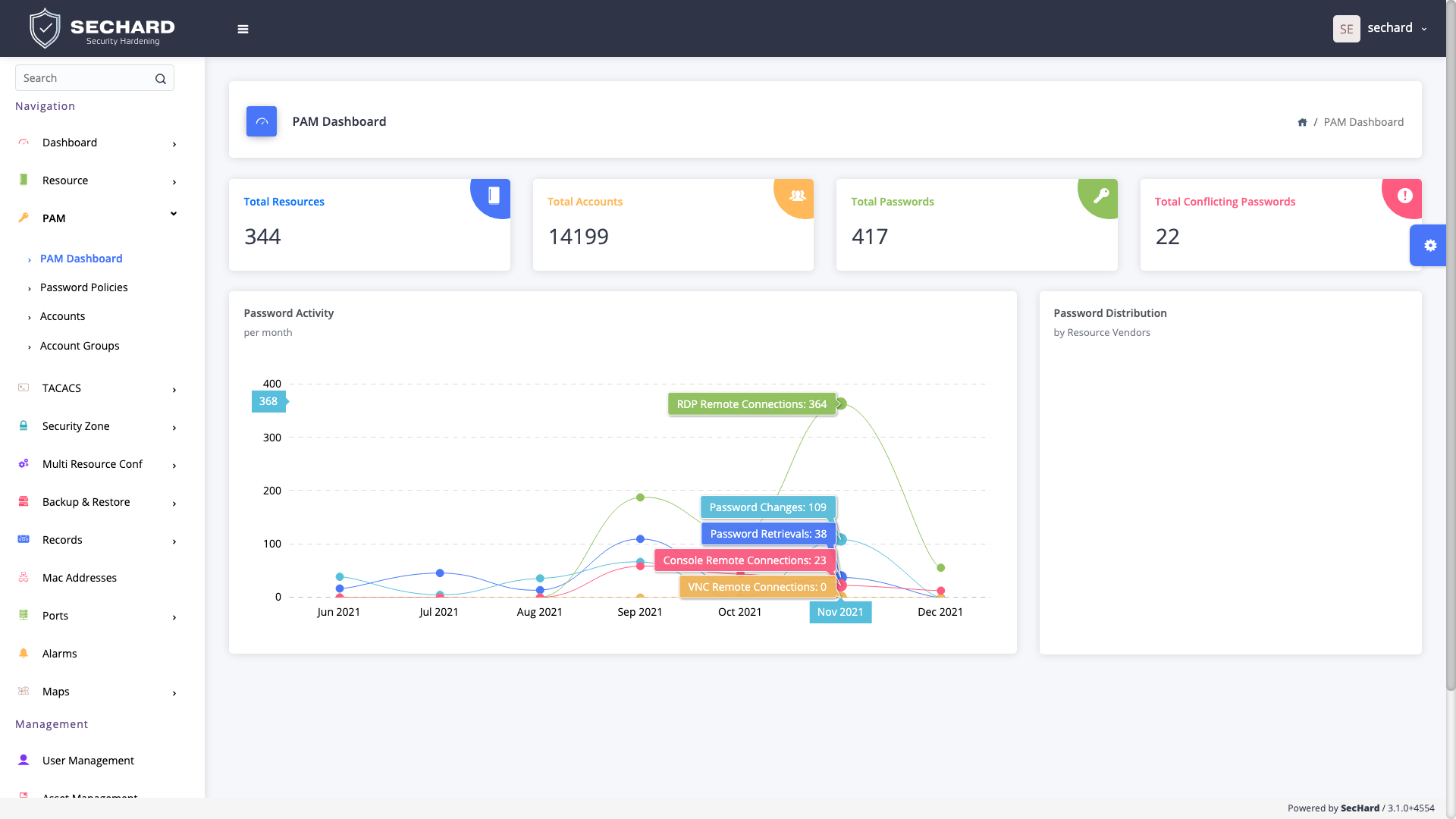
This does not mean SecHard does not have traditional PAM features. Like all other PAM products, SecHard has a password vault. It can enable the accesses such as RDP, VNC, SSH, and Telnet without knowing the password and can record all the sessions both in video and text format.
Do you already have a PAM product? Don’t worry. SecHard can integrate with third party PAM products and it can score their security hardening, as well.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
