In an era where cyber threats evolve unprecedentedly, relying solely on manual security management can be a kin to bringing a knife to a gunfight. Today’s cybersecurity landscape’s sheer complexity and dynamism necessitate more efficient, responsive solutions. Manual security management, while foundational and often unavoidable, involves human operators configuring, monitoring, and maintaining security systems—tasks increasingly outpaced by modern cyberattacks’ speed.
Why should we care about the “real costs” of manual security management? While the financial burden is a concern, focusing solely on dollar figures misses the bigger picture. Manual systems consume budget and drain precious time and resources, often introducing risks that are difficult to quantify but dangerous to ignore. By relying on older, more labor-intensive practices, organizations may inadvertently expose themselves to vulnerabilities that could have been avoided through automation or other advanced security solutions.
In this article, we will delve deep into the real costs of manual security management, breaking them down into three core dimensions: time, risks, and resources. By unpacking each of these aspects, we aim to provide you with a holistic understanding of what’s at stake when you choose manual processes over more streamlined, automated options. Whether you’re a security expert or a business leader, understanding these costs is the first step toward making more informed, strategic decisions about your organization’s cybersecurity posture.
onent of an organization’s network meets the same rigorous standards.
Increased Exposure Time
In cybersecurity, the longer a system is exposed to potential threats, the greater the likelihood of a successful attack. Manual systems inherently require more time for everything from deployment to threat detection, thus widening the window of vulnerability. The increased exposure time associated with manual operations gives attackers more opportunities to infiltrate systems, escalate privileges, or exfiltrate data.
Missed Threats
Even the most vigilant human monitoring is bound to miss some signs of a security event due to the sheer volume of data or the nuanced nature of modern cyber threats. Automated systems are designed to catch these elusive threats by constantly analyzing patterns and behaviors across a wide range of data points. While no system is foolproof, relying solely on manual oversight significantly increases the chances of missing critical threats, leaving organizations unknowingly exposed to risk.
Resources Required
Labor Costs
Manual security management often necessitates a larger workforce to handle the array of tasks that could be automated. Whether it’s constant monitoring, log analysis, or manually applying patches, these activities require skilled personnel whose salaries can significantly inflate operational costs. This financial burden grows as the organization expands or the security landscape becomes more complex, demanding even more labor to maintain the status quo.
Resource Allocation
Focusing on manual security management incurs high labor costs and diverts skilled staff from other, potentially more impactful, business areas. Tasks like strategic planning, network optimization, or new technology adoption may need to be addressed or completed as IT professionals are tied up with the minutiae of manual security tasks. Redirecting resources from these valuable business-enhancing activities to routine maintenance represents a hidden but substantial cost.
Infrastructure
Manual security management often demands specialized hardware or software to facilitate manual processes. The costs add up, whether additional servers to store logs or specialized monitoring software requiring manual input. Although essential for manual systems, these tools still require human operation, adding another layer of expenditure to an already costly operation.
Scalability Issues
As an organization grows, the limitations of manual security management become increasingly evident. The more complex the network, the more labor-intensive it becomes to oversee security manually. Adding new devices or adopting new technologies requires more effort in a manual system. The scalability issues inherent in manual security systems necessitate either a steep increase in resource allocation or a compromise on security effectiveness—both of which come at a high cost.
The Way Forward
Automation as a Solution
Automation emerges as a robust solution to the challenges presented by manual security management. Automating repetitive tasks like monitoring, patch deployment, and incident response significantly reduces human error and frees up valuable time. This leads to more efficient use of resources and can lower operational costs. Additionally, automated systems provide real-time data and analytics, which can be crucial for making informed security decisions quickly.
Strategic Planning
Incorporating automation into your cybersecurity strategy is a tactical move and a strategic imperative. Automated systems can be tailored to align with your business goals and security needs, providing a flexible yet sturdy framework for future growth. This facilitates a more agile response to the evolving cybersecurity landscape. Automation also allows your security team to focus on more complex, strategy-oriented tasks, providing a more comprehensive and effective defense against an increasingly sophisticated array of threats.
Conclusion
Manual security management can result in significant costs across multiple dimensions—time, risks, and resources. Not only do such systems consume a disproportionate amount of time for deployment and monitoring, but they also leave room for human error and security inconsistencies. These vulnerabilities often culminate in a higher risk profile for the organization, with missed threats and increased exposure time—the labor and infrastructure costs further strain already limited resources, with scaling up posing its financial challenges.
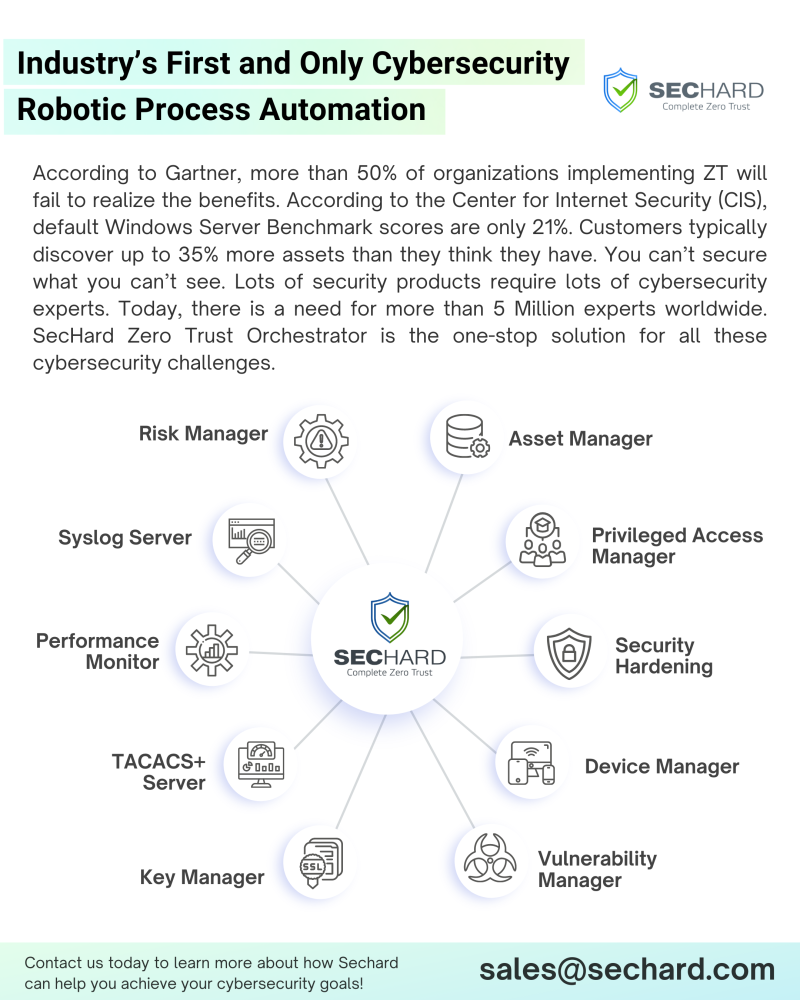
Manual systems’ sheer complexities and vulnerabilities make a compelling case for transitioning to automated solutions. Automated security management, like SecHard Zero Trust Orchestrator, offers an efficient and effective approach to meeting today’s cybersecurity challenges. This comprehensive solution consolidates multiple modules like Security Hardening, Privileged Access Manager, Asset Manager, Vulnerability Manager, Risk Manager, Device Manager, Performance Monitor, SSL Key Manager, TACACS+ Server, and Syslog Server, ensuring your security infrastructure is not only robust but also compliant with standards like NIST SP 800-207, the Executive Office of Presidential Memorandum (M-22-09), and Gartner Adaptive Security Architecture.
Given these insights, we encourage you to critically evaluate your current security management approach. To simplify and streamline the security hardening process, consider implementing SecHard Zero Trust Orchestrator. Its scalability and adaptability make it an investment that pays dividends in bolstering your security posture while facilitating compliance with industry standards.
Don’t leave your cybersecurity to chance. Contact us at [email protected] or Book a free demo today at https://lnkd.in/dt6PPvTr and see firsthand why SecHard is the ideal cybersecurity partner for your organization.