Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.


Automated Security Controls Assessment (ASCA) is an emerging technology that plays a crucial role in enhancing cybersecurity by continuously evaluating the effectiveness of security controls within an organization. This assessment is vital in a landscape where cyber threats are evolving rapidly, necessitating organizations to adopt more efficient and effective security measures.
Overview of Automated Security Controls Assessment (ASCA)
ASCA involves utilizing automated platforms to evaluate security controls—policies, procedures, and technical measures designed to protect information systems. Traditional manual assessments are often time-consuming and prone to human error, making ASCA a more reliable alternative. Automated tools can perform continuous monitoring, automated scanning, risk assessment, and generate detailed reports, allowing organizations to quickly identify and address vulnerabilities.
Benefits of Automated Security Controls Assessment (ASCA)
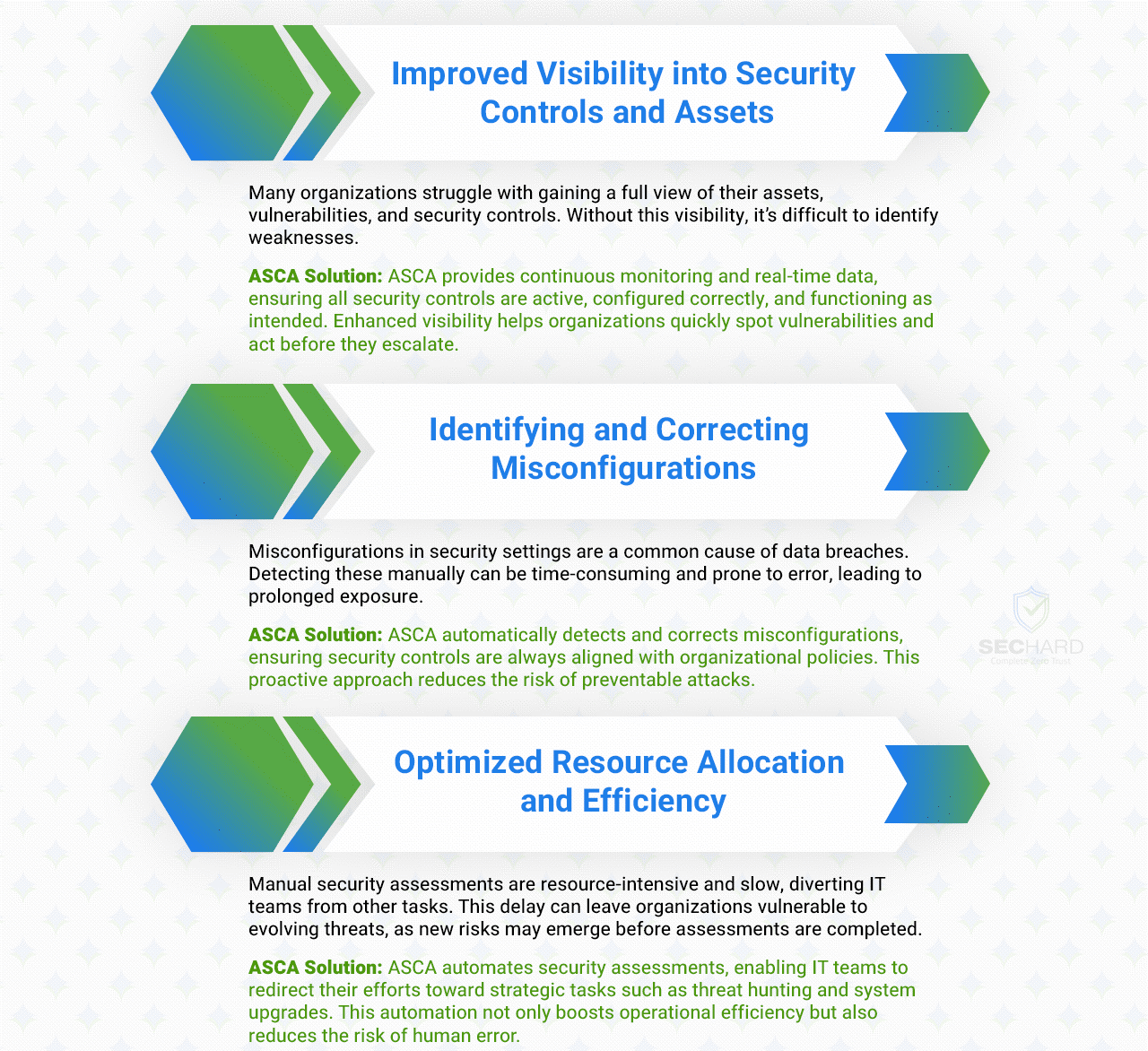
Automated Security Controls Assessment (ASCA) offers organizations a streamlined approach to evaluating their security posture by utilizing automated tools to assess and verify the effectiveness of implemented security controls.
Faster Security Control Evaluations
One of the most significant advantages of Automated Security Controls Assessment is its ability to drastically reduce the time needed for security evaluations. Traditional manual assessments are time-consuming, often requiring extensive labor hours to inspect and validate each control across the organization.
Improved Consistency in Assessments
Human error is a common factor that can affect the reliability of manual assessments. Differences in experience, fatigue, and focus can result in inconsistencies when evaluating security controls. Automated Security Controls Assessments eliminate this variability by applying the same criteria and checks uniformly across all systems, ensuring more consistent and repeatable results.
Real-Time Feedback for Immediate Action
ASCA tools provide near-instantaneous feedback on an organization’s security status. Traditional security assessments can take days or weeks to produce results, potentially allowing attackers to exploit vulnerabilities that remain unchecked during that window.
Adaptability for Growing IT Environments
As organizations expand, their IT environments grow increasingly complex. Manual security assessments can struggle to keep up with the scale of large organizations, especially when dealing with multiple locations, systems, or cloud services.
Cost Savings Over Time
Although there is often an upfront cost associated with implementing ASCA tools, they tend to be far more cost-effective in the long term. Manual assessments require significant labor and time investments, and frequent re-assessments are often needed to keep pace with evolving threats.
SecHard’s Automated Security Controls Assessment (ASCA) Solution:
SecHard is designed to make Automated Security Controls Assessment (ASCA) more effective, reliable, and tailored to your organization’s needs. With our ASCA solution, you get real-time visibility into your security posture, enabling continuous monitoring and automated assessments across your network, endpoints, cloud environments, and more. SecHard’s solution goes beyond just identifying vulnerabilities; it integrates with your existing security tools, providing in-depth remediation guidance to ensure issues are addressed quickly and accurately.
Our platform scales effortlessly as your organization grows, meaning no matter the size or complexity of your infrastructure, SecHard can continuously assess security controls, reduce human error, and free up your security team to focus on more strategic tasks. By using SecHard’s ASCA, you can ensure not just compliance but real-time operational resilience, while cutting down on the time and costs traditionally associated with manual assessments.
SecHard’s Security Hardening and Vulnerability Manager provide automated assessments and real-time monitoring, ensuring the organization stays ahead of security challenges while optimizing resources.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
