Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.


Continuous Control Monitoring (CCM) is a proactive approach within an organization’s governance, risk management, and compliance (GRC) framework. It involves the automated monitoring of control systems and processes to ensure their effectiveness and compliance with regulatory standards and internal policies. CCM provides real-time insights into potential risks, enabling organizations to identify and address issues before they escalate.
Cyber Hygiene Platform is a multi-module software for implementing Cyber Hygiene Holistic designed to facilitate compliance with the Executive Office of Presidential memorandum (M-22-09), NIST SP 800-207, and Gartner Adaptive Security Architecture. It also supports compliance with CBDDO compliance, CIS V7.1, CIS V8, CMMC Compliance, HIPAA compliance, ISO 27001, ISO 27002, NIST 800-1712, NIST 800-207A, NIST 800-210, NIST 800-535, PCI DSS, SOX Compliance. GDPR. KSA SAMA, KSA ECC. Eavpt Financial Cyber Security Framework Digital v1 compliance. SecHard Cyber Hygiene Platform is built on the principles of zero-trust security. which means it treats all devices and users as untrusted and verifies every access request before grantina access.
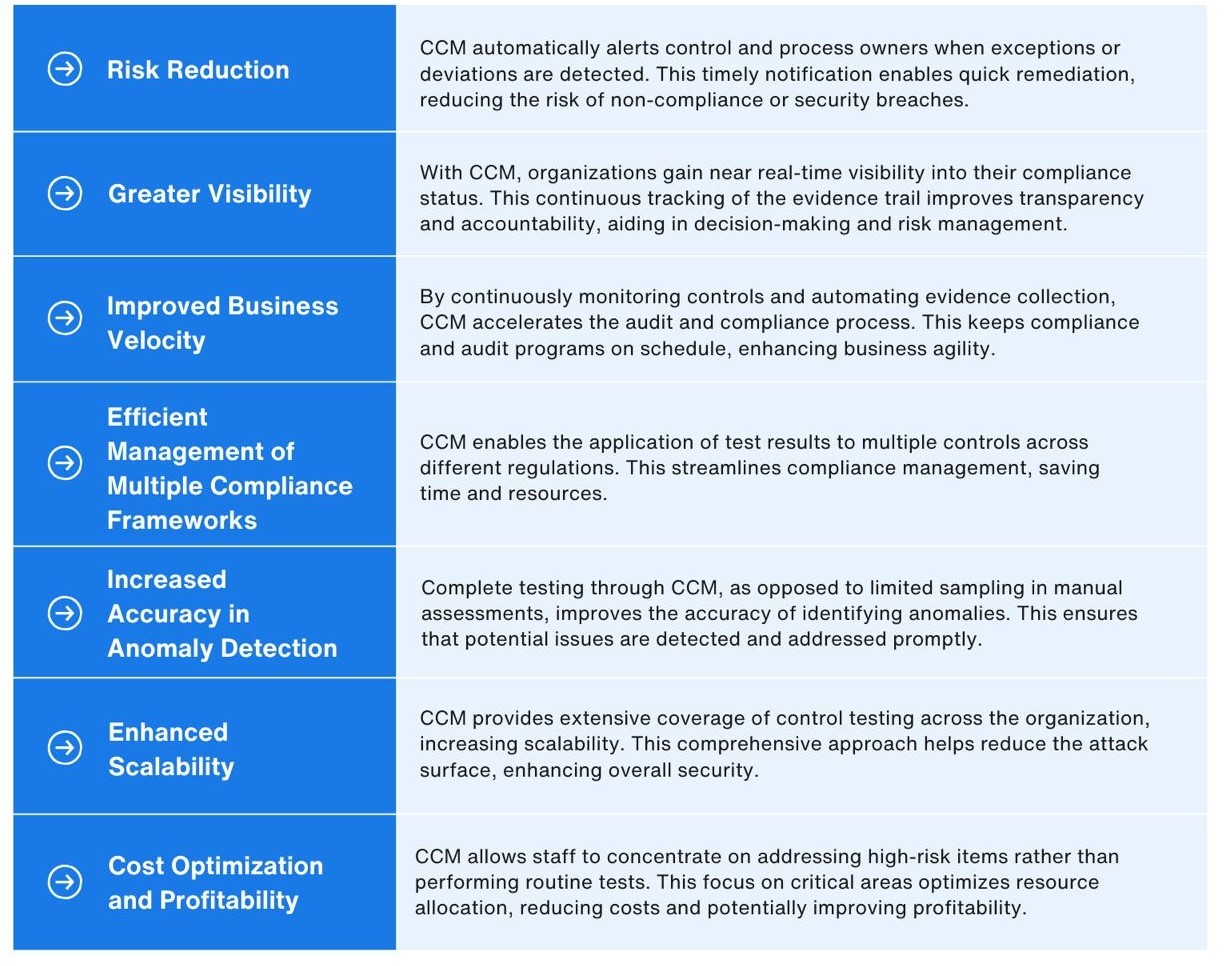
CCM enables organizations to detect and respond to risks in real time. By continuously monitoring controls, companies can identify anomalies, errors, or fraudulent activities as they occur, rather than after the fact. This proactive approach helps mitigate potential risks before they escalate into significant issues.
Staying compliant with regulations and industry standards is crucial for avoiding fines and maintaining a good reputation. CCM helps organizations maintain continuous compliance by ensuring that controls are consistently applied and functioning as intended. This continuous oversight reduces the likelihood of non-compliance and helps organizations meet their regulatory obligations more efficiently.
Manual control monitoring can be time-consuming and prone to human error. CCM automates the monitoring process, reducing the need for manual intervention and allowing staff to focus on more strategic tasks. This automation leads to greater accuracy, efficiency, and productivity within the organization.
By identifying and addressing issues early, CCM can help prevent costly incidents and reduce the financial impact of risks. Additionally, the automation of control monitoring processes reduces the need for extensive manual audits and reviews, resulting in significant cost savings over time.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
