Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.

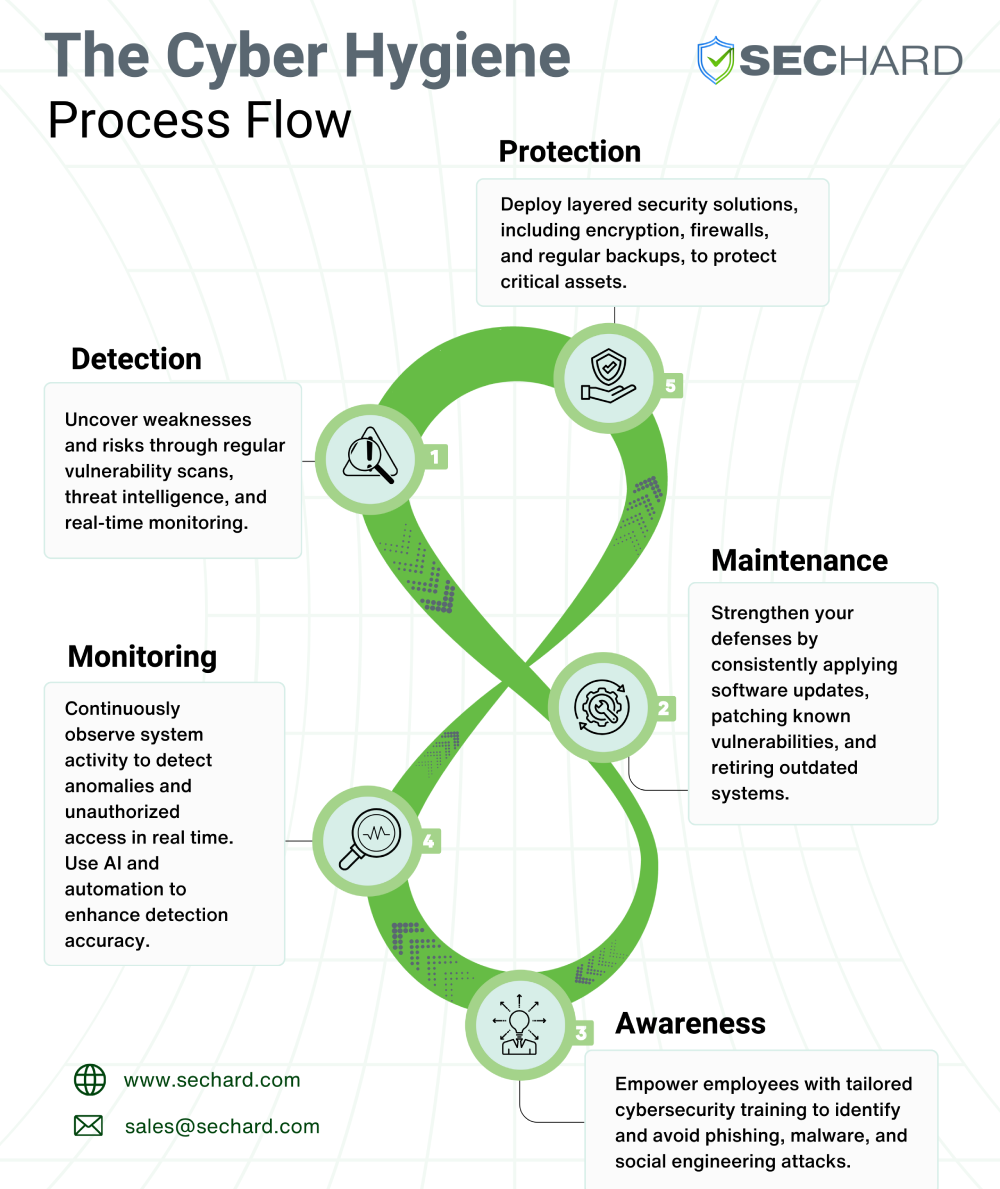
As we step into 2025, it’s time to get serious about cyber hygiene. Think of it as a fitness routine—not for your body but for your digital systems. Cyber threats are evolving faster than ever, and staying ahead requires more than just reactive fixes. Regular maintenance, smart habits, and proactive strategies can make all the difference in safeguarding your digital assets. The goal? To stop cyberattacks before they even have a chance to start.
So, what exactly is cyber hygiene? Simply put, it’s the set of everyday practices that keep your systems clean, secure, and ready to face whatever threats come your way. Just as personal hygiene helps prevent illness, cyber hygiene keeps malware, ransomware, and data breaches at bay.
Adopt Passwordless Authentication: Move towards passwordless solutions where feasible, reducing the risk of credential theft.
Utilize AI-Driven Password Managers: These tools adapt to user behavior, enhancing security without compromising convenience.
Implement Biometric Verification: Use biometric methods as a standard second factor for authentication.
Automate Patch Management: Use AI-powered systems to prioritize updates based on risk assessments.
Regular Vulnerability Scans: Conduct scans to identify potential weak points in your systems.
Rollback Features: Implement automated rollback features for problematic updates to ensure stability.
Implement Zero Trust Architecture: Ensure that every user and device is continuously verified before granting access.
AI-Driven Network Monitoring: Utilize tools that provide real-time threat detection and response capabilities.
Quantum-Resistant Encryption: As quantum computing poses new threats, prioritize encryption protocols that can withstand these advancements.
Regular Security Training: Conduct ongoing training sessions to help employees recognize and respond to potential cyber threats.
Gamified Learning Experiences: Use engaging methods to teach employees about cybersecurity best practices, making learning more effective.
At SecHard, we empower organizations to elevate their cybersecurity posture by integrating advanced Cyber Hygiene practices into everyday operations. Our solutions are designed to tackle the most pressing challenges of 2025, including password management, patch automation, and employee training, while ensuring robust network security and data protection.
Seamless Password Solutions:Transition to passwordless authentication and integrate AI-driven password management tools for enhanced security and convenience.
Automated Patch Management:Leverage our systems to prioritize and deploy updates efficiently, reducing risks without disrupting operations.
Comprehensive Employee Training:Gamified and interactive cybersecurity training programs ensure your team is always prepared to recognize and combat threats.
With SecHard by your side, you can confidently implement practical, forward-thinking cyber hygiene practices that protect your critical assets and prepare your organization.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
