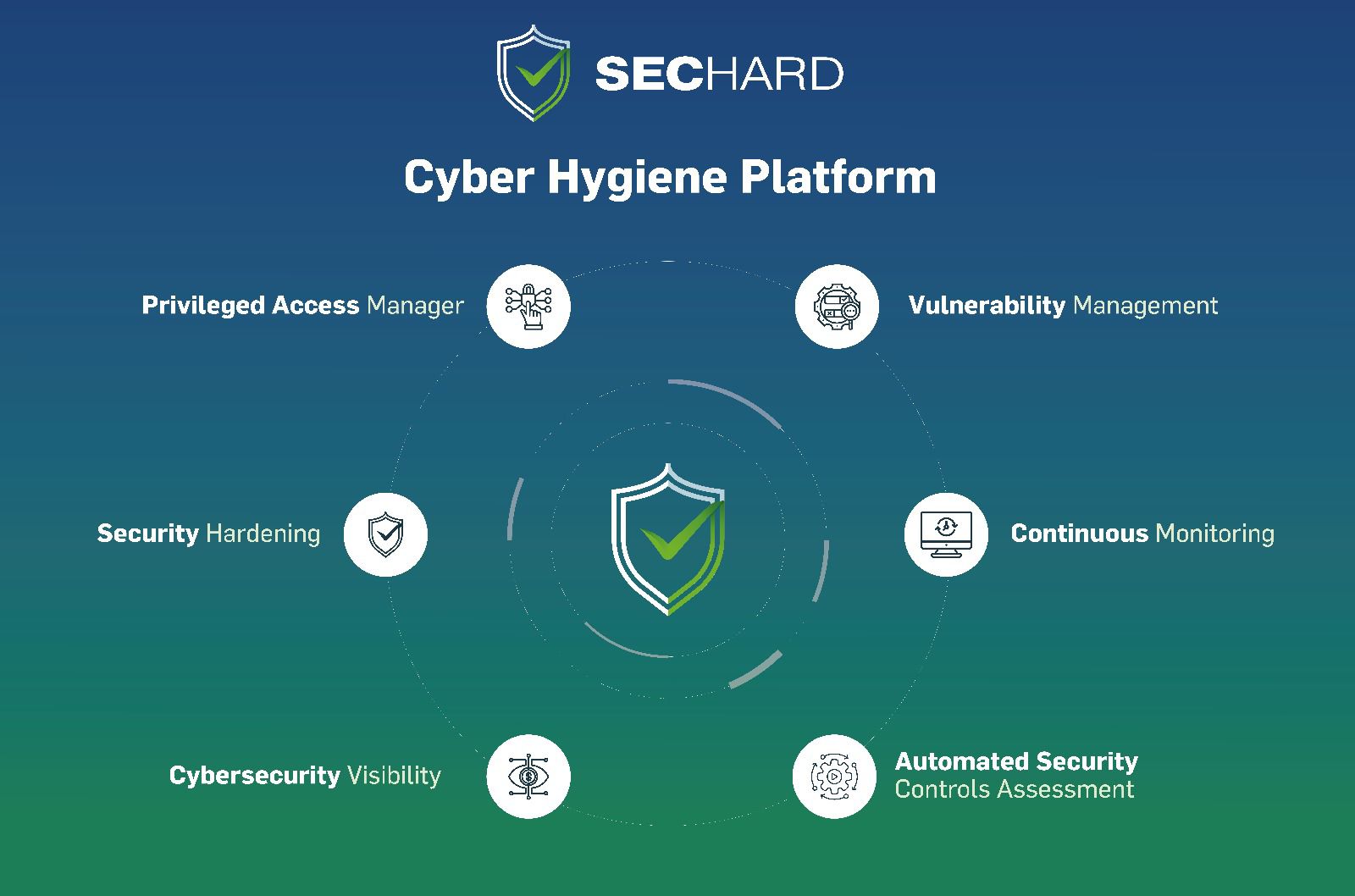
Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.

Think of your digital environment like your home. You wouldn’t leave your front door open, would you? That’s where ‘proactive detection’ steps in. It’s the digital equivalent to checking your locks and windows before you leave the house or installing a security system to alert you of any unusual activity.
Now, imagine you’ve got a great security system in place, but your front door is old and creaky. That’s where ‘maintenance and awareness’ come in. It’s like replacing that old door with a new, reinforced one and teaching your family not to open the door to strangers.And finally, it’s not enough to just lock up and leave. You need ‘continuous monitoring and robust protection’. This is your 24/7 security guard, your top-of-the-line CCTV system, and your safe with a fancy digital lock.
So, how about taking a look at our infographic for a tour of your new digital home security plan?
As cyber threats become increasingly sophisticated, strengthening your cyber hygiene is essential for safeguarding your organization’s digital assets. By implementing the above practices, organizations can build a resilient cybersecurity posture capable of adapting to emerging challenges today and in the future. Why does Cyber Hygiene matter now more than ever? Because the cost of inaction is steep. Cyber hygiene isn’t just about avoiding threats; it’s about preserving trust, meeting compliance standards, and ensuring your systems are always ready for business. Regular updates, smart password management, and employee awareness are no longer optional: they’re essential.

SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
