Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.


In the digital age, cybersecurity is paramount for organizations to safeguard their assets and mitigate risks. Cybersecurity Asset and Risk Management involves identifying, assessing, and managing the cybersecurity risks associated with an organization’s assets. Here are some key components and benefits of implementing a robust cybersecurity asset and risk management strategy:
The first step in cybersecurity asset and risk management is identifying and classifying all assets within the organization. This includes hardware, software, data, and network components. Proper classification helps in understanding the value and criticality of each asset, which is essential for prioritizing security measures and resource allocation.
Once assets are identified, the next step is to conduct a thorough risk assessment. This involves identifying potential threats and vulnerabilities that could impact the assets. By analyzing the likelihood and potential impact of these risks, organizations can develop a risk profile that informs their cybersecurity strategy.
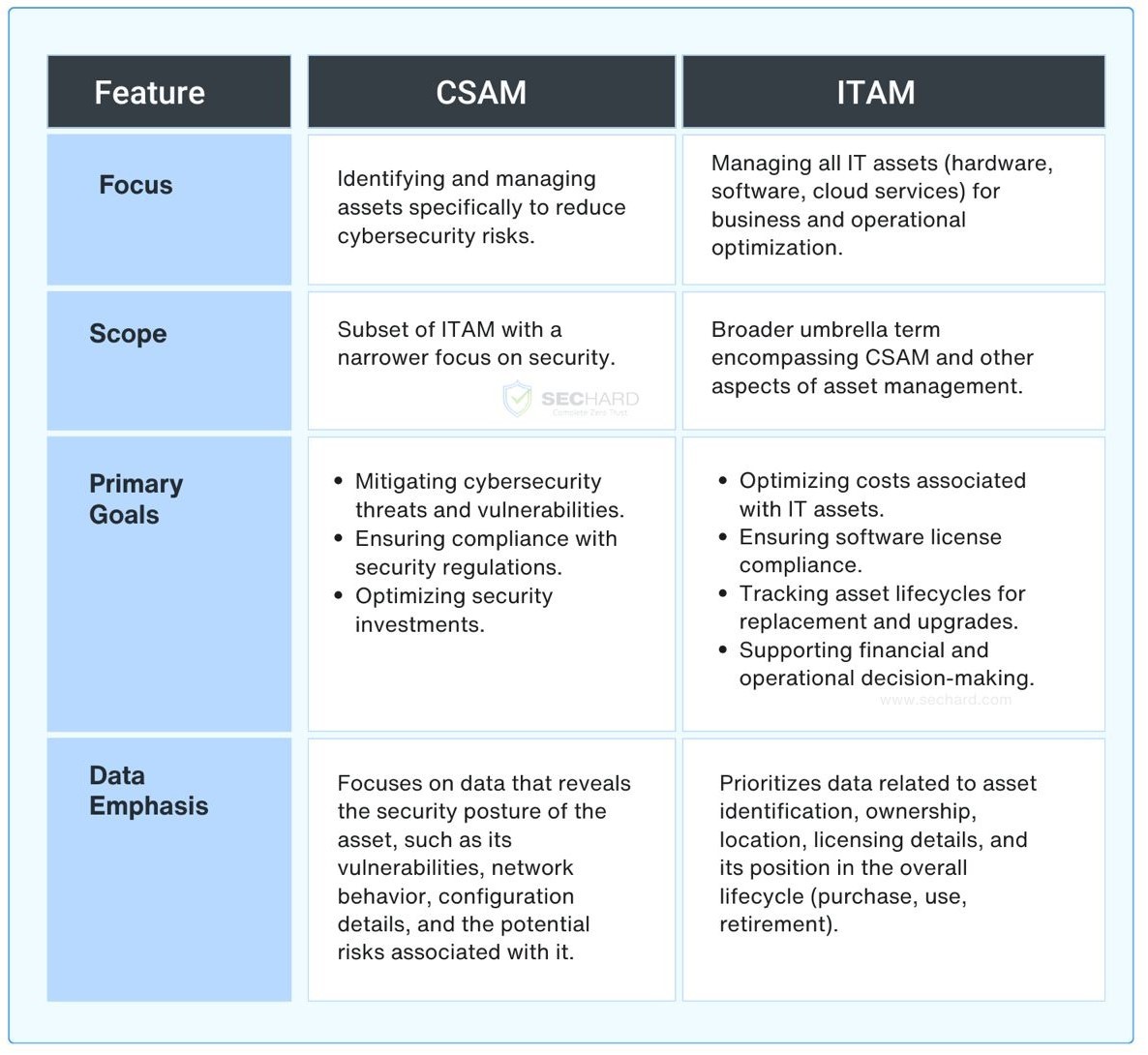
CSAM is a crucial component of ITAM. While both practices share commonalities in terms of discovering, cataloguing, managing, and tracking assets, they each play unique roles within their respective domains. ITAM manages all IT assets, while the more specialized CSAM focuses on cybersecurity. ITAM handles licensing and support, while CSAM prioritizes security by analyzing asset function and protection within the network. While both CSAM (Cybersecurity Asset Management) and ITAM (IT Asset Management) involve tracking and managing IT assets, they have distinct goals and priorities. Understanding these differences is crucial for choosing the right tools and processes to enhance your organization’s security posture and overall IT efficiency. This post outlines the key distinctions between CSAM and ITAM. SecHard provides automated security hardening auditing, scoring, and remediation for servers, clients, network devices, applications, databases, and more.
According to CIS, in order to have a secure operating system, it is necessary to change approximately four hundred security settings on a Microsoft Windows Server running with the default settings. There are most probably hundreds of missing security settings on the computer that you have. In an enterprise network with hundreds or thousands of IT assets, reporting and remediating all these deficiencies can be an operation that will take years for IT teams.
With SecHard, enterprises can easily add their own, unique controls and run them on thousands of different assets. In this way, special audit and automatic remediations can be produced for both common and non-common technologies such as Operating Systems, Network Devices, Applications, IoT, SCADA, Swift, POS and many more.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
