Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.

Cybersecurity mesh architecture (CSMA) provides a foundational support layer that enables distinct security services to work together to create a dynamic security environment.
CSMA provides a more consistent security posture to support increased agility for the composable enterprise. As organizations invest in new technology to enable digitalization, CSMA provides a flexible and scalable security foundation that provides bolt-on security for assets in hybrid and multi-cloud environments.
CSMA creates a better defensive posture through a collaborative approach between integrated security tools and detective and predictive analytics. The outcome is enhanced responsiveness to breaches and attacks.
Cybersecurity technology delivered through this model takes less time to deploy and maintain while minimizing the potential for security dead ends that cannot support future needs. This frees cybersecurity teams for more value-added activities.
Combat the increase in security complexity by evolving your security infrastructure to be more integrated, focusing on centralized administration and decentralized policy enforcement.
Position the enterprise for a secure future by choosing cybersecurity technologies that ease integration via plug-in APIs that allow extensions and customization, standards support, and extensible analytics.
Close interoperability gaps between different vendor solutions using current and emerging security standards.
Deploy supportive layers for a long-term CSMA strategy by choosing a primary vendor-led approach and filling capability gaps or using a best-of-breed approach. Make the most of CSMA’s supportive layers: security analytics, identity fabric, policy management, and integrated dashboards.
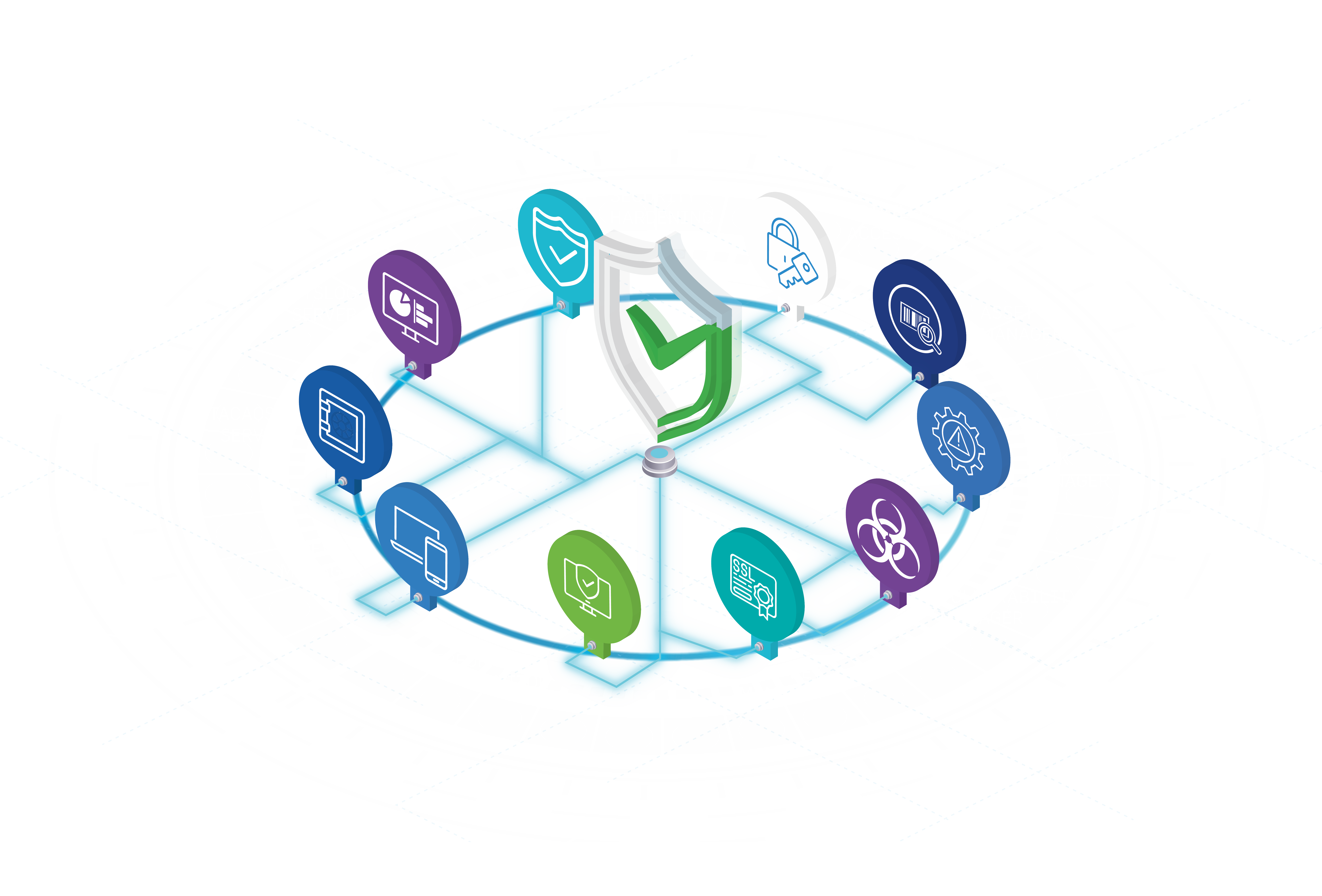
Cyber Hygiene Platform, a multi-module software for implementing Cyber Hygiene Holistic designed to facilitate compliance with NIST SP 800-207, the Executive Office of Presidential memorandum (M-22-09). Cyber Hygiene Holistic is a key cybersecurity mesh component. With Sechard, you can have a consolidated set of tools that work together seamlessly to protect your entire network.
Sechard’s multi-module software is designed to implement Cyber Hygiene Holistic, a key cybersecurity mesh component. With Sechard, you can have a consolidated set of tools that work together seamlessly to protect your entire network.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
