Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.

According to Gartner, more than 50% of organizations implementing Cyber Hygiene will fail to realize the benefits. According to the Center for Internet Security (CIS), default Windows Server Benchmark scores are only 21%. Customers typically discover up to 35% more assets than they think they have. You can’t secure what you can’t see. Lots of security products require lots of cybersecurity experts. Today, there is a need for more than 5 Million experts worldwide. SecHard Cyber Hygiene Platform is the one-stop solution for all these cybersecurity challenges.
In an era where digital threats evolve at an unprecedented pace, the need for robust and adaptive cybersecurity solutions has never been greater. Introducing the industry’s first and only Cybersecurity Robotic Process Automation (RPA) – a groundbreaking innovation that revolutionizes how organizations protect their digital assets.
Our Cybersecurity RPA leverages cutting-edge technology to automate complex security processes, ensuring real-time threat detection, swift incident response, and continuous monitoring of your IT infrastructure. By integrating advanced machine learning algorithms and artificial intelligence, our solution not only identifies potential vulnerabilities but also adapts to emerging threats, providing a proactive defense mechanism.
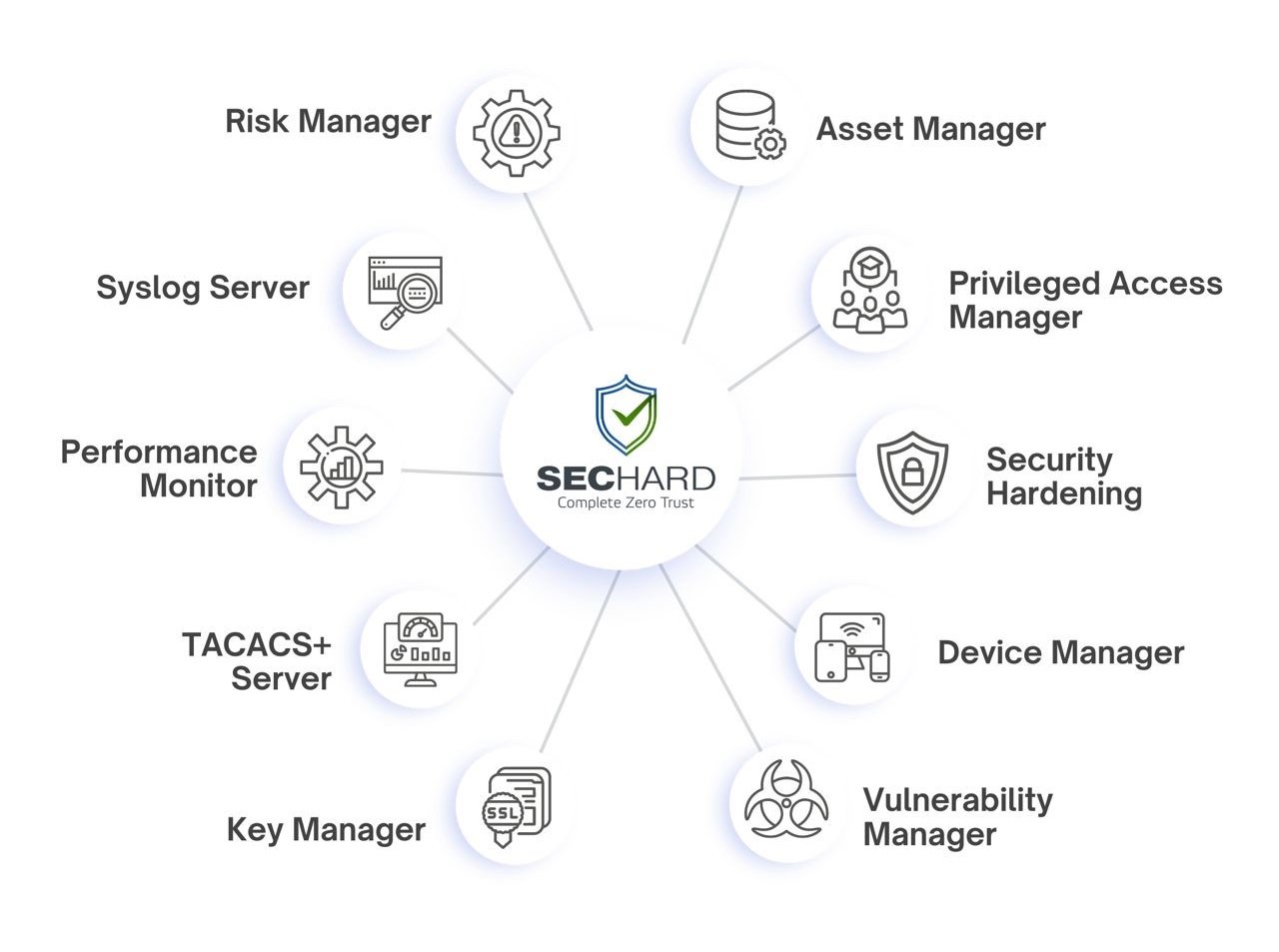
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
