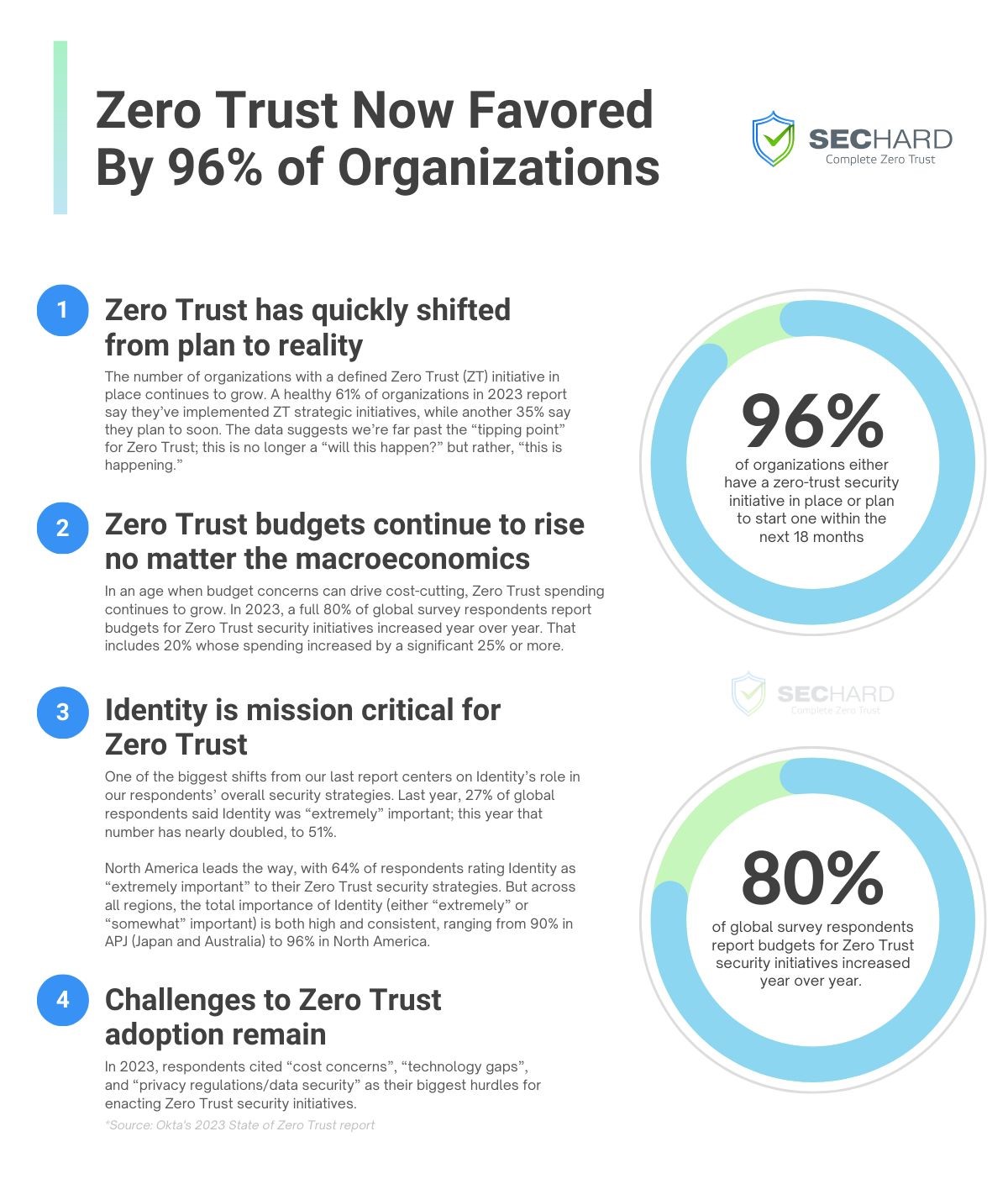
Security Hardening
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.


SecHard Zero Trust Orchestrator is a multi-module software for implementing Zero Trust Architecture designed to facilitate compliance with NIST SP 800-207, the Executive Office of Presidential memorandum, and Gartner Adaptive Security Architecture. It is built on the principles of zero-trust security, which means it treats all devices and users as untrusted and verifies every access request before granting access.
Zero Trust is a security strategy that assumes that everything on a network is hostile or compromised. It’s based on the principle of “never trust, always verify”. This means that users and devices are never trusted by default, and user identity verification is always needed to access an organization’s systems and data. Zero Trust’s goal is to restrict user access as much as possible without unduly hindering the business. It can help reduce a network’s attack surface, prevent lateral movement of threats, and lower the risk of a data breach.
SecHard provides automated security hardening auditing, scoring, and remediation for servers, clients, network devices, applications, databases, and more. According to CIS, in order to have a secure operating system, it is necessary to change approximately four hundred security settings on a Microsoft Windows Server running with the default settings. There are most probably hundreds of missing security settings on the computer that you have. In an enterprise network with hundreds or thousands of IT assets, reporting and remediating all these deficiencies can be an operation that will take years for IT teams. With SecHard, enterprises can easily add their own, unique controls and run them on thousands of different assets. In this way, special audit and automatic remediations can be produced for both common and non-common technologies such as Operating Systems, Network Devices, Applications, IoT, SCADA, Swift, POS and many more.
Verify Explicitly
Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies. This principle requires users to verify who they are, using more than one method, so that compromised accounts gained by hackers aren’t allowed to access your data and apps. This approach also requires devices to be recognized as being allowed to access the environment and, ideally, to be managed and healthy (not compromised by malware).
Use Least Privileged Access
Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to help secure both data and productivity. This principle limits the blast radius of a potential breach so that if an account is compromised, the potential damage is limited. For accounts with greater privileges, such as administrator accounts, this involves using capabilities that limit how much access these accounts have and when they have access. It also involves using higher-levels of risk-based authentication policies for these accounts.
SecHard provides automated security hardening auditing, scoring and remediation for servers, clients, network devices, applications, databases, and more.
A powerful identity and access management software to get compliant with Cyber Hygiene and to prevent attacks like privilege abuse, ransomware and more!
SecHard solves the risk awareness problem in asset management. Automated discovery, access, identify and remediation features provide ultra-wide visibility for all regulations.
With the passive scanning method, SecHard operates the vulnerability detection and management processes for all IT assets without creating any risks.
SecHard auto-discovers the certificates in companies’ environment, reports the expiration dates of these certificates, and it can automatically renew some of these certificates through well-known certificate authorities.
SecHard's unique risk assessment formula calculates the real-world risk scores by combining asset group risk scores, security hardening scores, and vulnerability scores.
Powerful and customizable network device management with backup/restore, configuration change detection, performance monitoring, bandwidth monitoring, and firmware upgrade.
Integrated performance and availability monitoring for servers, network devices, databases, applications, IoT, and industrial control systems.
Centralized Authentication, Authorization and Accounting (AAA) for *nix systems and network devices with Microsoft Active Directory integration.
Simplified log management across network devices and servers, real-time alarms based on critical events, log forwarding in Syslog and CEF formats.
Book a meeting with SecHard experts.
