In today’s rapidly changing cybersecurity landscape, where new threats emerge on a near-daily basis, the continued dependence on passwords for authentication presents a complex challenge. Passwords serve as both a critical first line of defense and a potential vulnerability, often becoming the focus of many attack methods to compromise digital assets. Hackers exploit the inherent weaknesses in password-based security systems with alarming efficiency, whether it’s the blunt-force approach of brute-force attacks or the more cunning psychological tactics employed in phishing campaigns.
Understanding the types of password attacks that one may encounter is not merely an intellectual endeavor; it’s a vital strategic necessity for any organization committed to safeguarding its digital assets. This article aims to delve deep into the various forms of password attacks, offering a comprehensive analysis of each—from the underlying techniques used by attackers to the potential repercussions and effective countermeasures. Learning the complexities of these forms of cyber aggression provides businesses and individuals with the vital insights needed to bolster their primary security measures, thereby strengthening their overall cybersecurity framework.
In an era where the digital realm is integral to business and personal life, falling victim to a password attack could result in far-reaching consequences, including financial loss and damage to reputation. Therefore, this article serves as both an educational guide and a call to action. It aims to equip you with the knowledge you need to recognize and defend against the most common types of password attacks, emphasizing the importance of a multi-layered security approach to protect against the varied tactics used by cybercriminals.
Most Common Types Of Password Attacks
Brute-Force Attacks: The Indiscriminate Lock Picker
Overview: Brute-force attacks are a tried-and-true method that involves an exhaustive, systematic effort to guess a password. While these attacks are relatively simple in concept, they are surprisingly effective at cracking passwords, especially those that are short or lack complexity. The goal is to leave no stone unturned by trying every possible combination until the correct password is found.
Technical Details: A brute-force attack can be resource-intensive and time-consuming, which often leads attackers to first target systems with weaker security policies. Specialized software and tools, such as John the Ripper or Hashcat, are used to automate the brute-forcing process.
The efficacy of a brute-force attack significantly improves with computational power; thus, attackers with access to powerful hardware or a botnet can drastically reduce the time needed to break a password. High-speed or distributed attacks can attempt thousands or even millions of password combinations per second, increasing the attack’s effectiveness.
Dictionary Attacks: The Lexicon of Vulnerability
Overview: Dictionary attacks represent a more targeted approach compared to brute-force tactics. Instead of attempting every conceivable combination, attackers utilize a curated list of probable passwords, often compiled from dictionaries, known leaks, or common password conventions. This method aims to exploit human predictability in password creation, targeting commonly used or previously compromised passwords.
Technical Details: Dictionary attacks often employ large databases known as “dictionary files,” which consist of an extensive list of common, easy-to-remember, or previously breached passwords. These lists can range from simple English words to complex combinations of alphanumeric characters.
The attack is typically automated, leveraging specialized software to cycle through the dictionary file rapidly. While not as exhaustive as a brute-force attack, dictionary attacks are generally faster and can be highly effective against systems where users employ commonly used or weak passwords.
Credential Stuffing Attacks: The Domino Effect of Reused Credentials
Overview: Credential stuffing attacks exploit the human tendency to reuse passwords across multiple platforms. In this kind of assault, attackers use a set of previously breached username and password combinations and try them across various services. Because many people reuse their credentials, the attacker can potentially gain unauthorized access to multiple accounts, escalating the damage far beyond the original breach.
Technical Details: The effectiveness of credential stuffing relies on the widespread practice of password reuse. Attackers use specialized bots or software to automate login attempts across numerous sites and services.
Typically, these attacks are facilitated by large-scale data breaches that leak username and password combinations, which are then tested on other platforms. While not sophisticated in its approach, the attack can be devastatingly effective due to the commonality of password reuse.
Phishing Attacks: The Art of Deception
Overview: Phishing attacks are unique in that they rely on human psychology and behavior rather than exploiting a software vulnerability. In these cases, attackers deceive users into voluntarily divulging their login credentials. Typically posing as a trusted entity, attackers craft misleading emails or messages that prompt users to enter sensitive information into a fraudulent website that mimics a legitimate service.
Technical Details: Phishing attacks often start with a seemingly innocent email that appears to be from a reputable source. These emails include links that direct users to a fake login page designed to collect their credentials. The success of this attack hinges on the attacker’s ability to convincingly replicate both the email and the website of a trusted organization.
Technological sophistication varies among phishing attacks; some may be easy to spot due to poor design or grammar, while others may convincingly replicate legitimate services, even using SSL certificates to display HTTPS in the address bar.
Keylogger Attacks: Silent Trackers
Overview: Keylogger attacks are particularly insidious as they operate quietly in the background, capturing every keystroke made on a compromised machine. This information often includes sensitive data like usernames and passwords, which the attacker can later use or sell. Since keyloggers can be either hardware-based or software-based, their detection and mitigation require a multi-faceted approach.
Technical Details: For software-based keyloggers, the malicious code is often delivered through phishing emails or malicious downloads. Once installed, the software records keystrokes and sends the data back to the attacker’s server.
Hardware-based keyloggers can be even more covert; they may take the form of USB devices or hardware implants physically connected to the target computer. Another sophisticated method involves acoustic analysis, where the attacker uses microphones to determine keystrokes based on the sounds made during typing.
Mitigating Diverse Forms of Password Attacks
In the never-ending battle against cyber threats, a multi-layered approach is not just advisable; it’s essential. Focusing solely on the technological aspects, like multi-factor authentication or account lockout mechanisms, can give an organization a false sense of security. These elements, although vital, are only one part of a comprehensive strategy. Password policies that enforce complexity and regular updates add another layer of defense, making it increasingly difficult for cybercriminals to breach your digital boundaries.
However, technology alone can’t provide a bulletproof shield. The human element, often considered the weakest link, can be transformed into an asset through proper education and awareness training. Employees who can spot phishing attempts and report them become an invaluable first line of defense, adding a layer of dynamic and adaptive resiliency. These educated users complement technological safeguards like real-time monitoring and anti-malware solutions, creating a more rounded and resilient defense posture.
This combination of technology and human intervention can be reinforced further with ongoing measures like regular security audits. By continually assessing the effectiveness of your technological defenses and training programs, you can adapt and update your strategies to address new and evolving threats. This continuous improvement model ensures that your organization remains vigilant and prepared, no matter how sophisticated or diverse the password attacks become.
In conclusion, mitigating diverse forms of password attacks is a multifaceted endeavor that requires both technological innovation and human vigilance. Organizations that adopt this holistic approach are far more likely to withstand the ever-increasing and evolving cyber threats. Make no mistake: the war against cyber threats is not a one-time battle but an ongoing campaign. The good news is that tools like SecHard Privileged Access Manager offer integrated solutions that cover both technological and human factors, making it easier to protect your organization effectively.
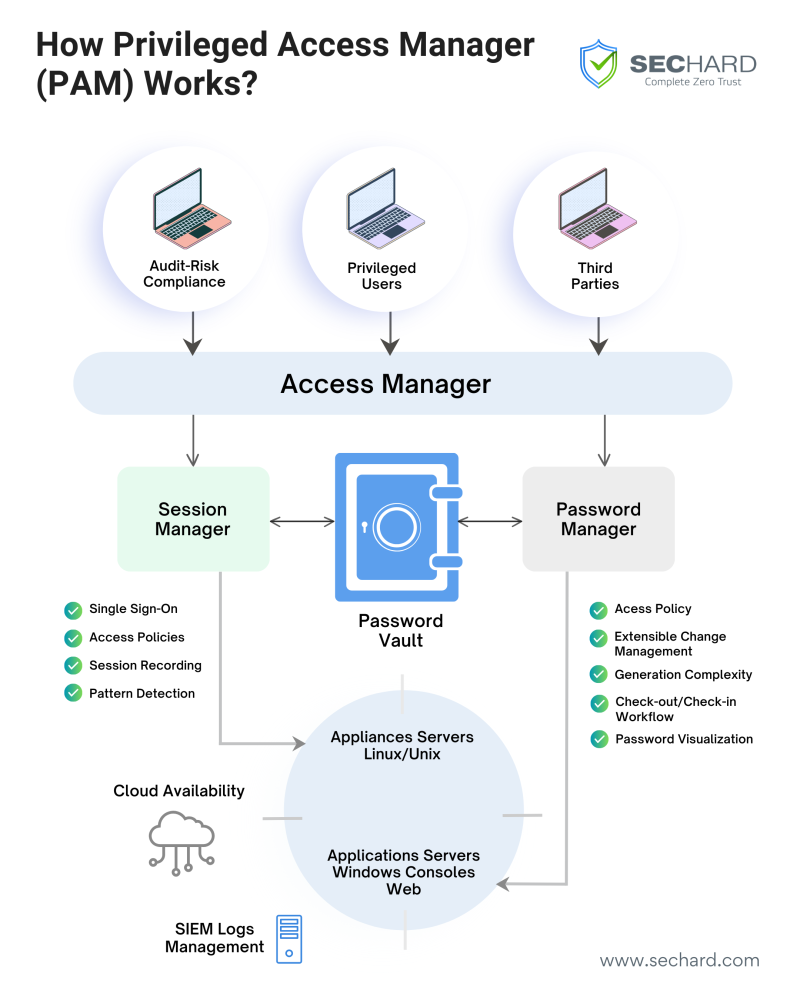
SecHard Privileged Access Manager
SecHard Privileged Access Manager has advanced features that offer unbeatable protection for your organization’s privileged accounts. From an encrypted password vault that securely stores all your critical credentials and comprehensive session recording capabilities that provide in-depth visibility into user activities to 2FA authentication, ensuring extra layers of security, SecHard Privileged Access Manager is your ultimate defense against cyber threats.
But that’s not all – our solution is more than a security tool. It’s designed to enhance operational efficiency, too. By automating routine tasks, reducing the potential for human error, and providing tools for seamless policy enforcement, SecHard Privileged Access Manager helps your organization save valuable time and resources.
Don’t leave your cybersecurity to chance. Contact us at [email protected] or Book a free demo today at https://lnkd.in/dt6PPvTr and see firsthand why SecHard is the ideal cybersecurity partner for your organization.